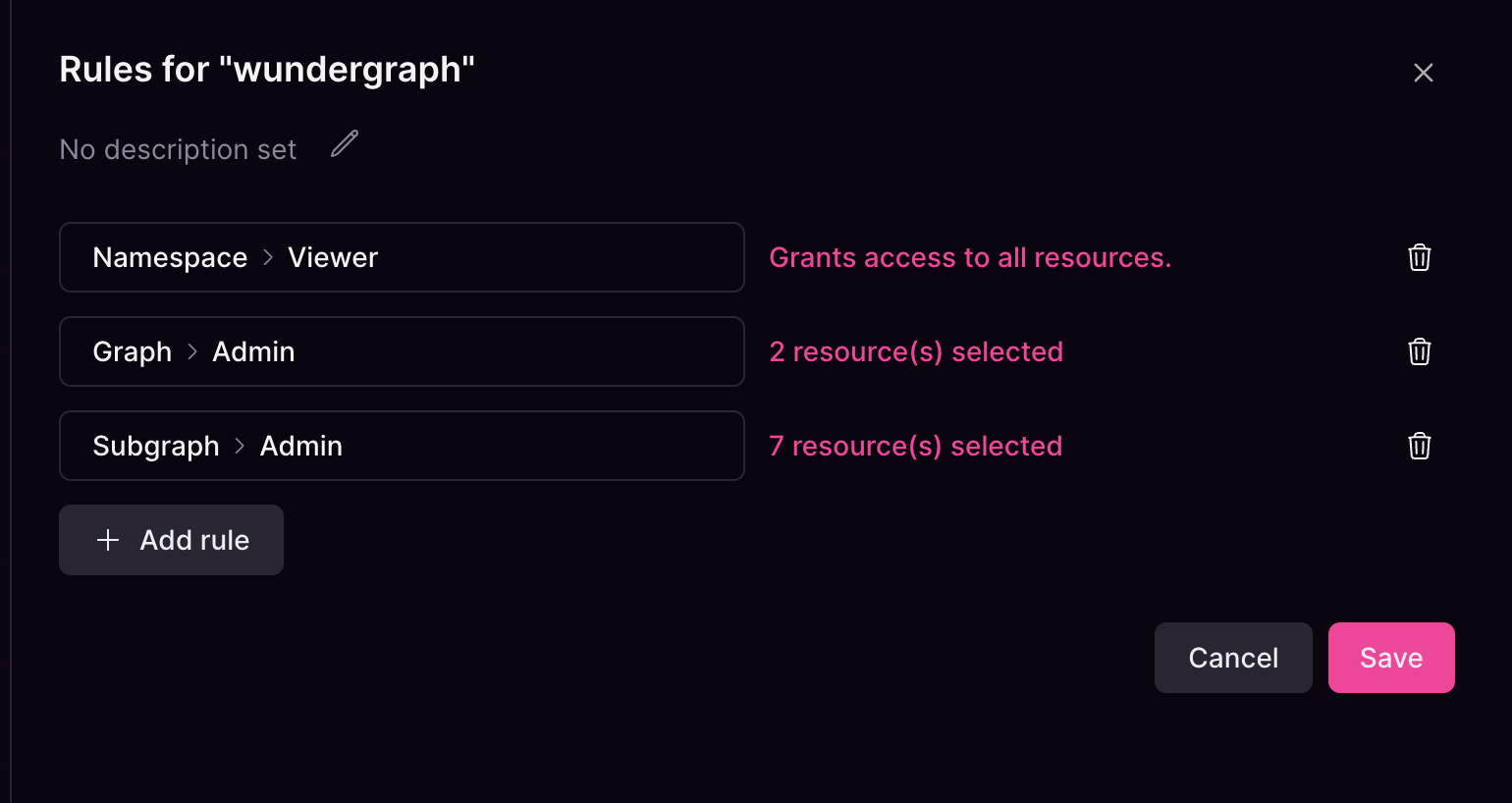
Group with no rules
Unlike assigning specific resources, if a group doesn’t have any rule assigned, this will result in the group effectively not having access to any resource.
Roles
You can assign multiple roles to a group using theAdd rule button. If no group rules are configured, group members will not have access to any resources.
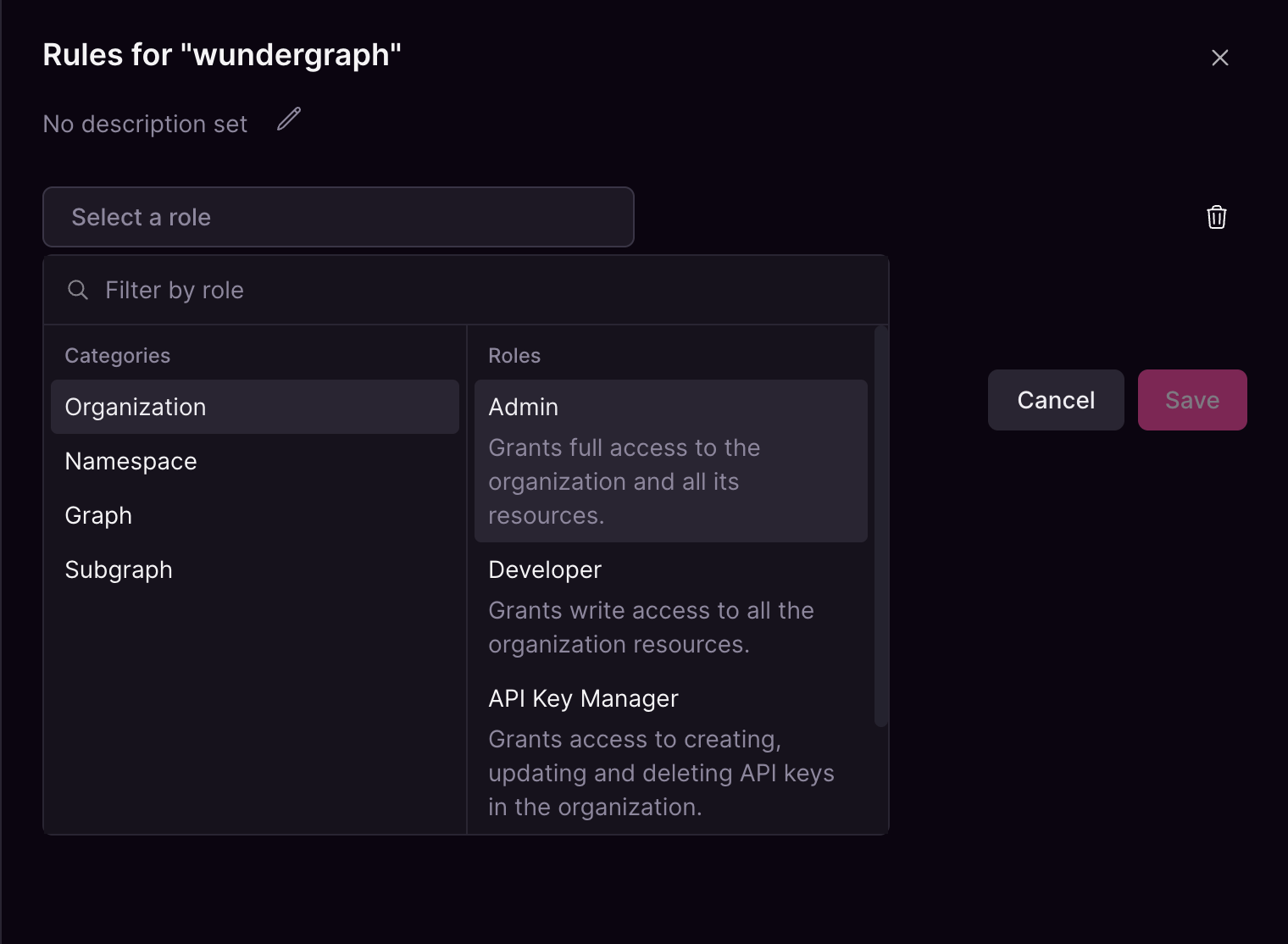
Role selector
Organization Admin and Organization Viewer roles in the same group, but you cannot assign the same role type more than once. You could also add a Graph Admin role to that group, as long as each role type appears only once.
The order in which roles are assigned does not affect how access checks are performed. For example, given the following group:
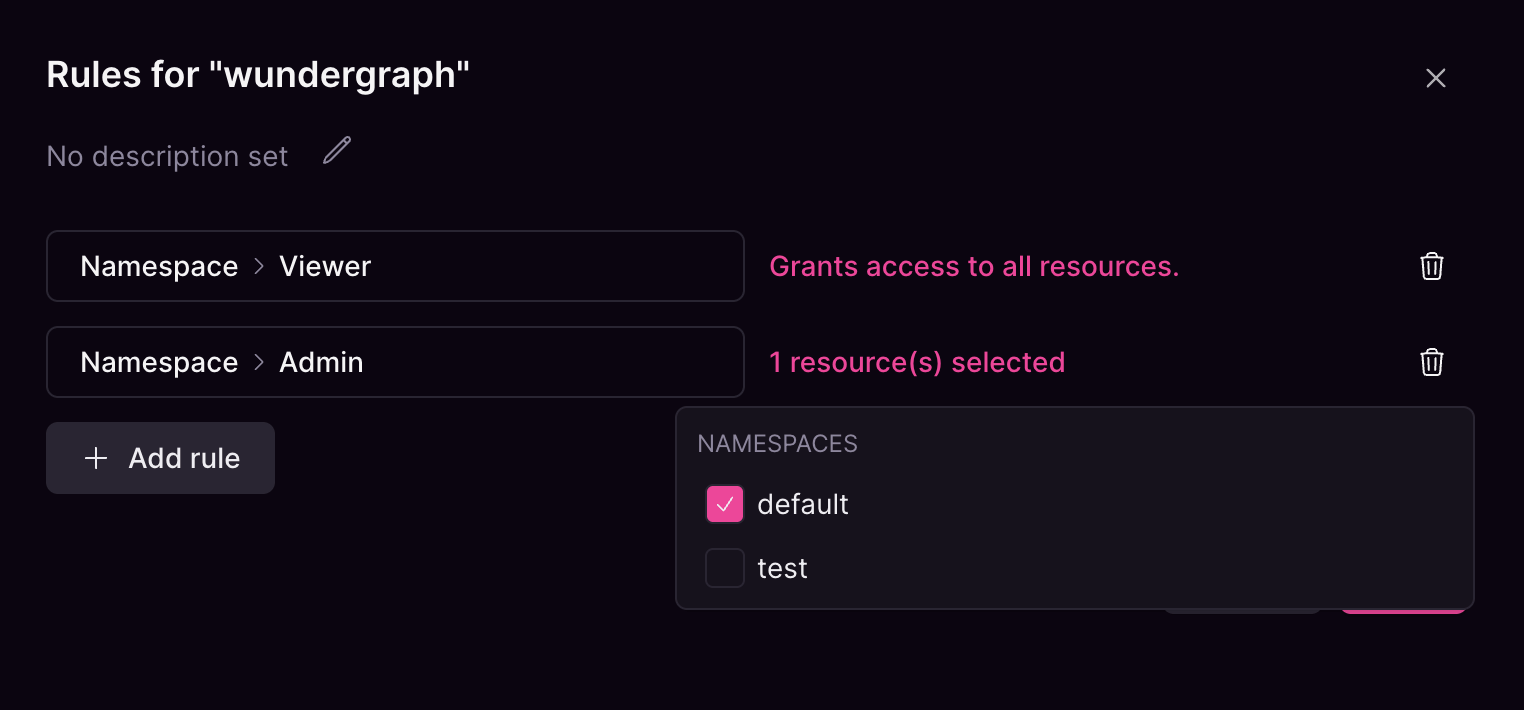
default namespace and Viewer to the test and any other namespace that may exist in the organization.
If the namespace default is deleted, the Admin role is no longer scoped and will apply to all resources.
With this in mind, members of the following example will have Organization Admin access to all resources.
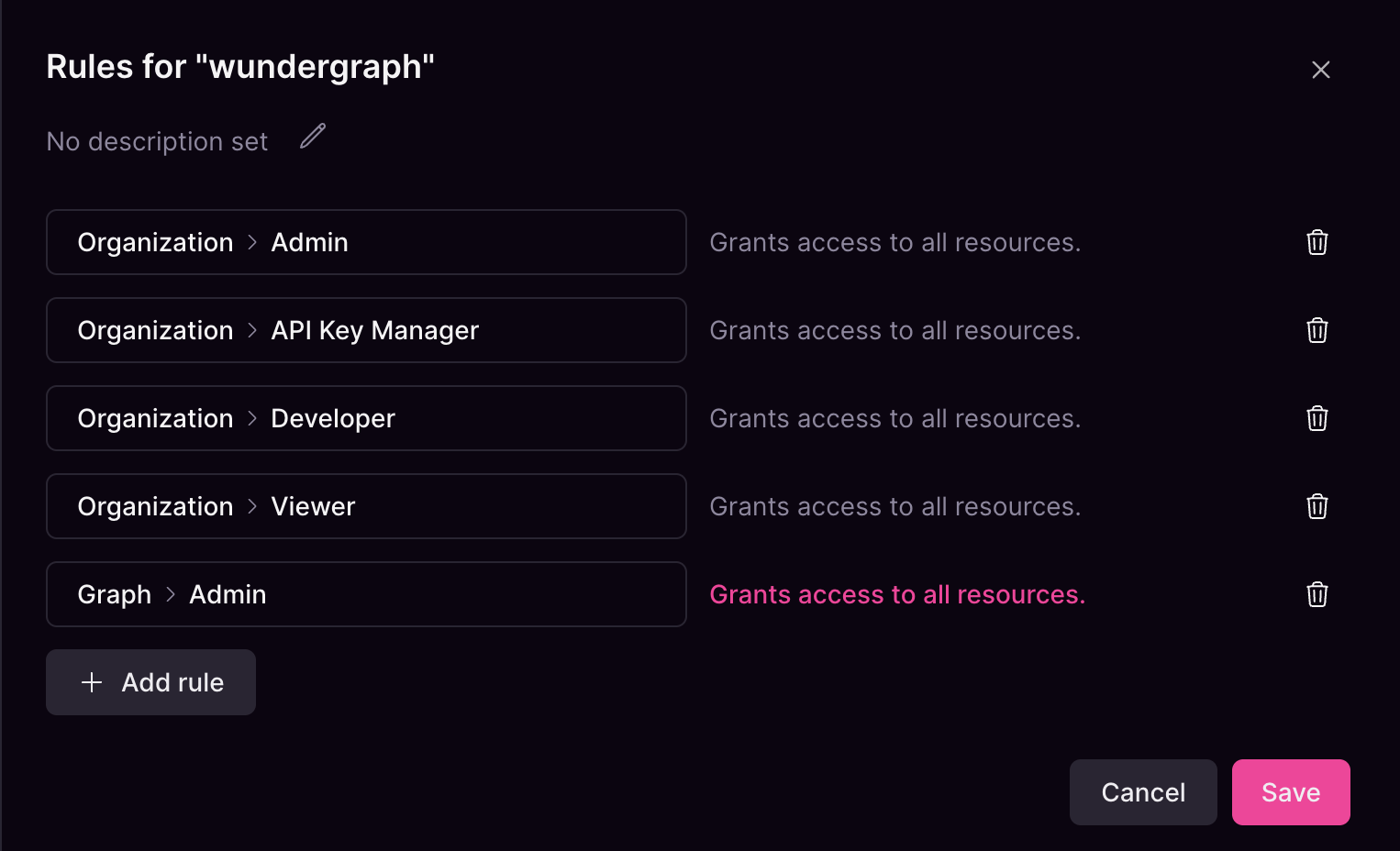
Organization Roles
These roles apply at the organization level and cannot be limited to specific resources:- Admin — Full permissions to create and manage all services.
- Developer — Read and write access to all organizational objects.
- API Key Manager — Permissions to create, modify, and delete API keys.
- Viewer — Read-only access to all organizational objects.
Namespace Roles
- Admin — Read and write access to assigned namespaces.
- Viewer — Read-only access to assigned namespaces.
Graph Roles
- Admin — Read and write access to assigned graphs.
- Viewer — Read-only access to assigned graphs.
- Namespace: Grants access to all graphs within the selected namespace, including permission to create new graphs.
- Specific graphs: Limits access to only the selected graphs.
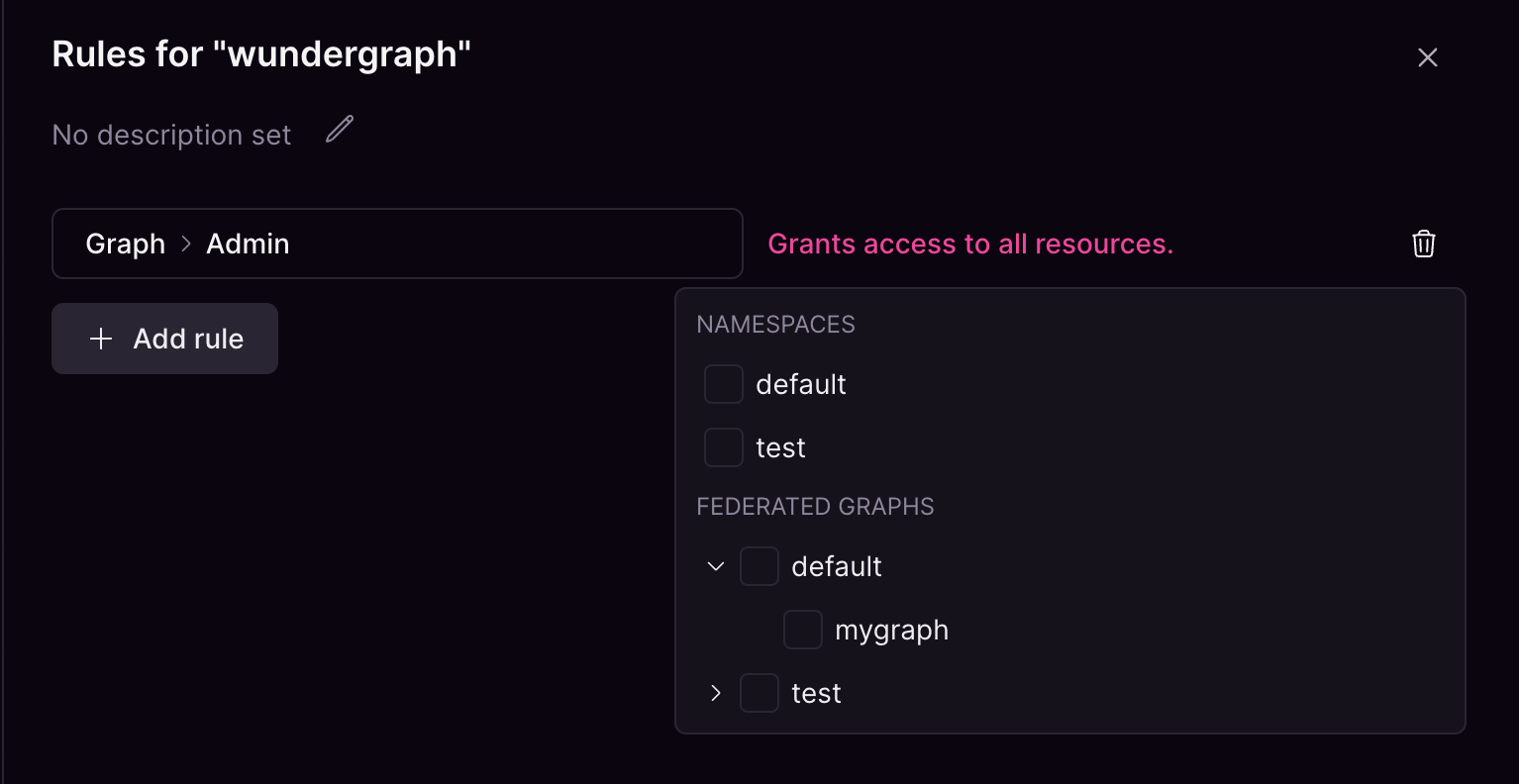
Graph resource selector
Subgraph Roles
- Admin — Read and write access to assigned subgraphs.
- Publisher — Read and write access to assigned subgraphs, but cannot create new ones.
- Checker — Grants read-only access to subgraphs as well as the ability to create subgraph checks.
- Viewer — Grants read-only access to subgraphs.
- Namespace: Grants access to all subgraphs within the selected namespace, including permission to create new subgraphs.
- Specific subgraphs: Restricts access to only the selected subgraphs.
Resources
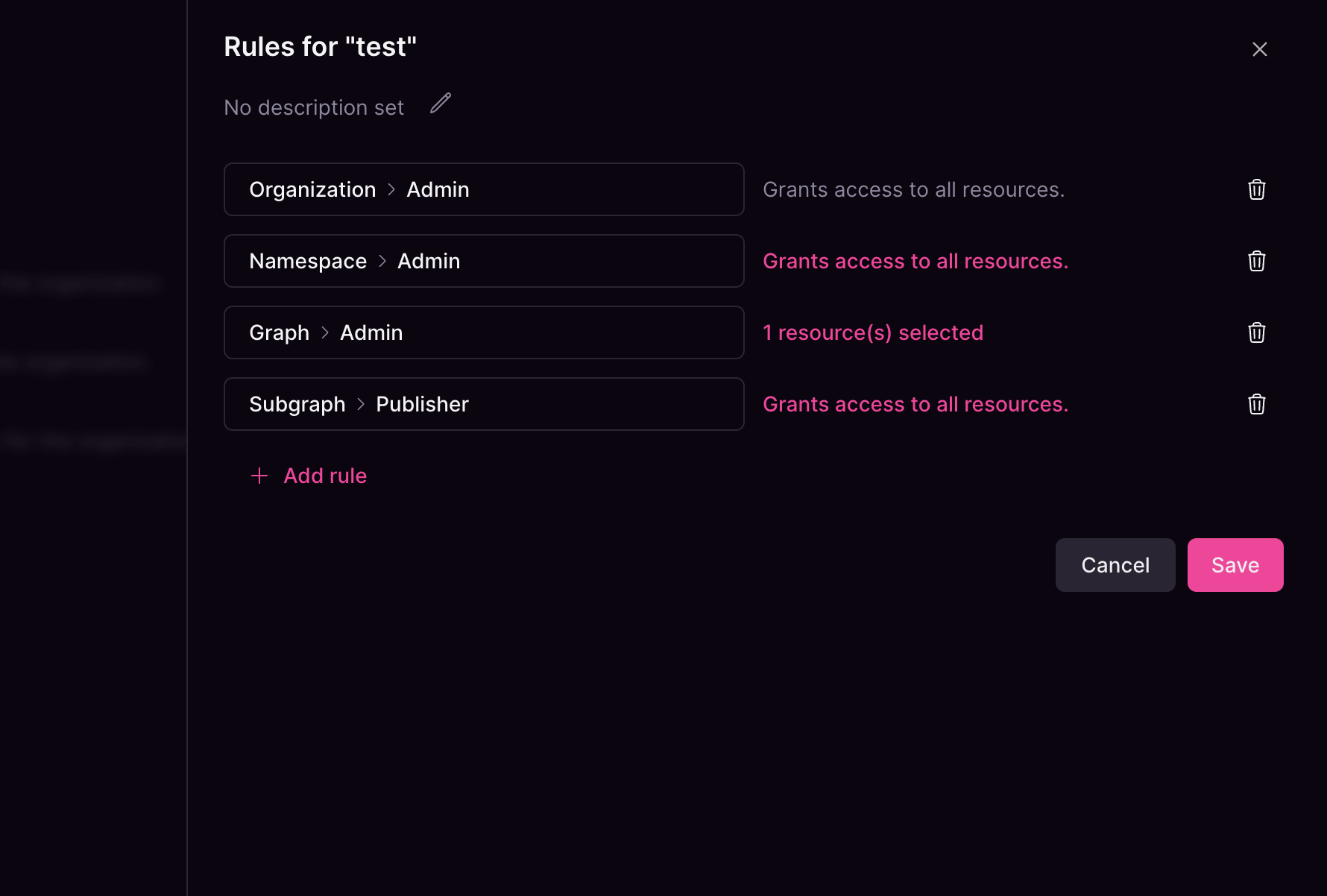
Graph resource selector
- Namespaces
- Federated Graphs
- Subgraphs